The Networking of Wireless Information Systems (NetWIS) laboratory led by Dr. Wenye Wang, is focused broadly on in-depth understanding, algorithm and protocol design in mobile wireless networks. Our vision is that by developing new models, measuring experimental results, and understanding basic properties of wireless networks in different circumstances, it is possible to design algorithms, protocols, and architectures that enable a wireless network to have robust architecture and topology and high performance for diversified applications and large-scale distributed, intelligent systems.
Our lab members include undergraduate students who gain their experience in research and prepare for their graduate study, and graduate students who aim to make novel contributions to wireless networking area. Currently, we are focused on the issues like mobile clouds, vehicle-to-vehicle communications, wireless in the Smart Grid from the perspective of network resilience and performance in the presence of failures and abnormality.
Fundamental Properties
The understanding of dynamics and randomness in mobile wireless networks can enable revolutionary versus evolutionary advances in the design and performance of a network. Our group is committed to the discovery, modeling, and investigation of basic properties, interaction among different network dynamics and requirements, with an emphasis on node mobility, routing operation, network topology, and performance. In particular, our efforts are being placed on developing new models of user mobility/profiles, which present the most challenges in wireless networks. Areas of current research interest include the following:
Mobility modeling is a fundamental issue in wireless mobile networks, which has a significant impact on research areas, such as routing protocol design, network performance evaluation, link and path lifetime analysis, network connectivity study and network topology control. Therefore, we are actively working on how to design a mobility model which can effectively mimic smooth transient moving behaviors of mobile nodes and have the desired steady state properties, such as stable node speed and uniform node distribution, is a challenging issue. We aim to design a mobility model which can i) achieve the above goals, ii) integrate a variety of nice properties of existing mobility models and iii) be flexible to mimic the realistic network scenarios.
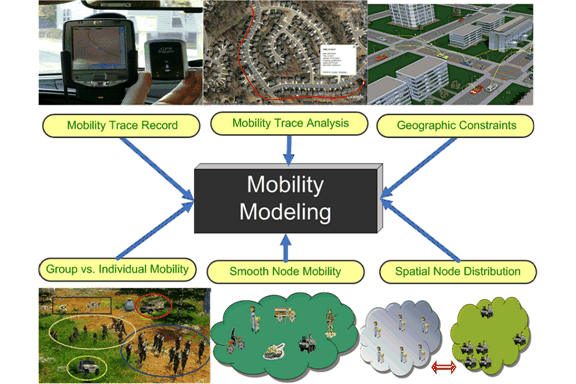
In order to provide better performance and quality of service, we develop a framework to capture user mobility profile (UMP) which is a combination of historic records and predictive patterns of mobile terminals and to estimate service patterns and locations of mobile users, including descriptions of location, mobility, and service requirements. We aimed to develop new mobility model to characterize not only stochastic behaviors, but historical records and predictive future locations of mobile users as well, that is, to incorporate aggregate history and current system parameters to acquire UMP. We are also interested in the characterization of mobility uncertainty and its impact on network topology.
Publications
- Ming Zhao and Wenye Wang, “A Unified Mobility Model for Analysis and Simulation of Mobile Wireless Networks,” submitted for journal publications, December 2006.
- Ming Zhao and Wenye Wang, “A Novel Semi-Markov Smooth Mobility Model for Mobile Ad Hoc Networks,” in the Proc. of IEEE GLOBECOM’06, (Best Paper Award), San Francisco, CA, November 2006.
- Ian F. Akyildiz and Wenye Wang, “A Predictive User Mobility Profile Framework for Wireless Multimedia Networks,” in IEEE/ACM Transactions on Networking, vol. 12, no. 6, pp. 1021-1035. Dec. 2004.
Understanding the link and path stochastic properties can greatly help researchers design mobility-resilient MANETs, maximize routing performance, optimize topology control, and achieve the desired network performance.
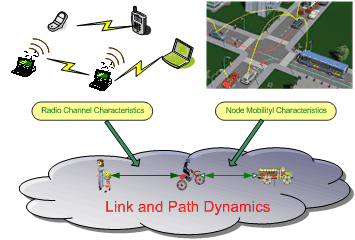
We are focused on developing new models to study link and path properties under the circumstances such as varying radio link conditions, node mobility, geographical constraints, and interferences. In particular, we aim to study probabilistic and statistical properties of link/path lifetime, link/path reliability in the presence of node or link failures due to radio channels and node mobility. Currently, we are developing an analytical model of the reliability problem in wireless ad hoc networks, as well as algorithms for computing two-terminal reliability in mobile ad hoc networks.
Publications
- Ming Zhao and Wenye Wang, “Analyzing Topology Dynamics in Ad Hoc Networks Using A Smooth Mobility Model,” in the Proc. of IEEE Wireless Communications and Networking Conference (WCNC), March 2007.
- Shawqi Kharbash and Wenye Wang, “Computing Two-Terminal Reliability in Mobile Ad hoc Networks,” in the Proc. of IEEE Wireless Communications and Networking Conference (WCNC), March 2007.
Compared with wired network, wireless ad hoc networks are more vulnerable to malicious attacks as well as failures due to their unique features, such as constrained energy, error-prone communication media and highly dynamic network topology. Especially, every node (or end user) may have quite different “social” behaviors. For example, selfish nodes refuse to forward packets for other nodes in order to save their own energy. While, with no intention for energy-saving, malicious nodes may launch all kinds of denial-of-service (DoS) attacks by replaying, reordering or/and dropping packets from time to time, and even by sending fake routing messages.
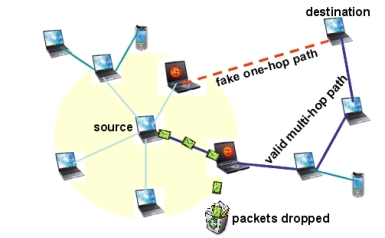
As we know, the cooperation of mobile nodes is critical to the normal operation of multi-hop wireless networks, thus all aforementioned misbehaviors have prompted open challenges to many issues, such as protocol design, service availability, and topology management, in mobile ad hoc networks. Therefore, we are investigating node behaviors in order to design a general node model so that we can have an in-depth understanding on the evolution of different node behaviors and their impact to network survivability. The modeling and analysis of node behaviors will yield new insights into the analysis and design of resilient wireless multi-hop networks.
Publications
- Fei Xing and Wenye Wang, ” On the survivability of Wireless Ad Hoc Networks in the Presence of Routing Malfunction,” in preparation for journal submission. April 2007.
- Fei Xing and Wenye Wang, ” Modeling and Analysis of Connectivity in Mobile Ad Hoc Networks with Misbehaving Nodes,” in Proc. of IEEE International Conference on Communications (ICC ’07), Vol. 4, pp. 1879-1884, June 2006.
Rapid and widespread deployment of Wireless Local Area Networks (LANs) offers great convenience to access the Internet via wireless devices such as laptop computers and portable data assistants (PDAs) users. However, wireless LANs are vulnerable to malicious attacks due to their shared medium in unlicensed frequency spectrum. Therefore, strong security features are required for a variety of applications in wireless LANs. Unfortunately, secure communications are not gained for free in wireless networks because all security protocols require transmission of users’ credentials for identity verification, control messages, as well as data encryption/decryption which cause degradation in quality of service (QoS). In addition, with the increasing demand for mobile applications, while security protocols are expected to be an integral part of network protocols, they should not undermine the usage of wireless networks because of their effects on system performance. Therefore, our focus is to investigate, via modeling, analysis, and experiments, to what extent system performance can be impacted by security protocols with respect to mobility scenarios, heterogeneous networks, and different applications.
Publications
- Avesh K. Agarwal and Wenye Wang, “On the Impact of Quality of Protection in Wireless Local Area Networks with IP Mobility,” in ACM-Springer Mobile Networks and Applications (MONET) Journal, Vol. 12, No. 1, pp. 93-110, February, 2007.
- Wenye Wang, Wei Liang, and Avesh K. Agarwal, “Integration of Authentication and Mobility Management in Third Generation and WLAN Data Networks”, in Wireless Communications and Mobile Computing (WCMC)- special issue on “WLAN/3G Integration for Next-Generation Heterogeneous Mobile Data Networks,” Volume 5, Issue 6, pp 665-678, September 2005.
- Wei Liang, Wenye Wang, “A Quantitative Study of Authentication and QoS in Wireless IP Networks,” in Proc. of IEEE INFOCOM’05, March 2005.
Design and Optimization
Essential to our vision for wireless networking is a focus on the design of protocols, algorithms for wireless networks that can optimize resource utilization, network architecture, and system performance. We are pursuing this general goal in different network platforms such as cellular networks, multi-hop networks, and low-power sensor networks, through studies in several topics.
Self-organization is a major issue in randomly deployed wireless sensor networks, and should be addressed subject to some important constraints such as sensing coverage, reliable data transport, energy efficiency, and fair load distribution. We propose to develop self-organization algorithms that can construct a network by sensors themselves without external supervision, while preserving coverage and connectivity under stringent energy and reliability constraints.
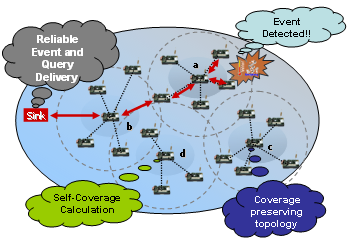
Particularly in dense networks, energy-efficient scheduling is a key factor to extend the functionality and lifetime of the network. That means, only the nodes maintaining the functionality stay active whereas others are scheduled to sleep, e.g., switching to power saving mode. Therefore, the energy dissipation in sending/receiving and idle time can be significantly reduced and by updating the sleeping nodes, network lifetime can be prolonged. The fundamental challenge of scheduling is to maximize the number of sleeping nodes to conserve more energy while maintaining the functionality of the wireless sensor networks. In our work, we integrated coverage and connectivity by a tiered approach; thus, nodes having been used for connectivity or coverage have different sleeping behaviors during an update interval. Nodes, which are not selected for coverage or connectivity-tier, are put into sleep immediately; nodes in the coverage-tier are put into semi-sleep because they can wake up for sending data and can go back to sleep mode periodically; nodes in the connectivity-tier stay active in order to forward data traffic. Hence, we enable more nodes to sleep while maintaining the coverage and connectivity of the network.
Notice that many applications developed for wireless sensor networks (WSNs) demand for reliable communication service, since majority of these applications are event-critical applications (e.g., fire monitoring, border surveillance, etc.), we also investigate the following question: “What is the information to be delivered reliably on WSN?“. Especially densely deployed sensor nodes can generate many redundant messages that essentially indicate the same from the area of interest, thus posing significantly high and unnecessary communication overhead. Therefore, we introduced a new concept for WSNs as event reliability and query reliability. Event reliability is defined to be achieved when every critical event report message is received by the sink node; query reliability is defined to be achieved when every query of the sink is received by those sensors that cover the entire sensible terrain within the area of deployment. Furthermore, we need to take many related issues into consideration such as congestion control, event differentiation, overhead for acknowledgment, and energy conservation.
Publications
- Nurcan Tezcan and Wenye Wang, “ART: An Asymmetric and Reliable Transport Mechanism for Wireless Sensor Networks,” in Journal of Wireless Sensor Networks (JSNet), February 2007.
- Nurcan Tezcan, Wenye Wang, Mo-Yuen Chow, “A Bidirectional Transport Mechanism in Wireless Sensor Networks,” in Proc. of the IEEE MILCOM’05, Atlantic City, NJ, USA.
- Nurcan Tezcan and Wenye Wang, “A lightweight Classification Algorithm for Energy Conservation in Wireless Sensor Networks, ” in Proc. of the 14th International Conference on Computer Communication and Networks (ICCCN’05), San Diego, California , USA , October, 2005.
The mobile ad hoc network (MANET) is a kind of self-configured network that fits into the needs of many special application scenarios where pre-deployment of network infrastructure is infeasible or unnecessary. In large-scale MANETs, the hierarchical structure has been proven effective in addressing the scalability problems. However, node mobility poses a big challenge to the network topology stability. The wireless links connecting the nodes are subject to frequent availability changes as the nodes move around. The paths between communicating nodes, therefore, experience disruptions from time to time.
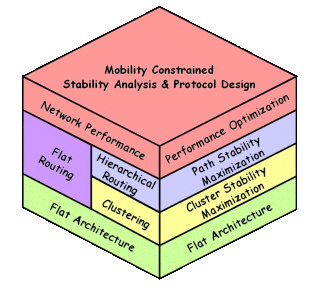
We are currently developing an analytical model to reveal the maximum architectural stability in hierarchical mobile ad hoc networks, which is measured by the lifetimes of clusters, inter-cluster links, and paths. The understanding of the stability bound then provides guidelines for us to design a new clustering algorithm and a new cluster-based routing protocol that work together to achieve this bound. The maximized topology stability can bring the performance benefits such as higher throughput, lower packet loss, and lower routing overhead than the previous clustering and routing schemes.
Publications
- Yi Xu and Wenye Wang, ” MEACA: Mobility and Energy Aware Clustering Algorithm for Constructing Stable MANETs,” in the Proc. of IEEE Milcom’06, Washington, D.C. October 2006.
User mobility, limited radio resources, and on-battery operations, along with multi-class services have been the main challenge for wireless networks, especially when mobile users move from one cell to another cell, or from one system to another system in that bandwidth or channels must be allocated prior to the arrival of mobile terminal. We have been focused on three major issues:
- Energy-efficient bandwidth allocation scheme for wireless networks: In this work, we study the intrinsic relationship between the energy consumption and transmission rates of mobile terminals, in which transmission rate is determined through channel allocations. Our objective is to reduce energy consumption of each terminal, while statistically meeting the requirements of quality of service (QoS) of each type of traffic.
- User mobility profiling and location tracking: The most salient feature of wireless networks is mobility support, which enables mobile users to communicate with others regardless of location. It is also the very source of many challenging issues, relating to the mobility and service patterns of mobile terminals, namely, user mobility profile (UMP). For each mobile user, a UMP consists of detailed information of service requirements and mobility models that is essential to quality of service (QoS)
and roaming support. Therefore, we proposed a generic framework that ca characterize not only stochastic behaviors, but historical records and predictive future locations of mobile users as well. - Inter-system location management: In heterogeneous wireless environments with different system specifications and radio frequencies, how to enable seamless roaming among these systems is one of the most important issues for mobile applications. Thus, we proposed a dynamic inter-system location management scheme, which is aimed to reduce signaling costs and improve system performance. The proposed scheme consists of two operations: inter-system location update and paging, in which bandwidth requirements, velocity, and network load are taken into account. In accordance with this scheme, a mobility application part (MAP) protocol is devised for location registration and call delivery processes to support roaming capability of mobile users moving across different network backbones and infrastructures.
Publications
- Wenye Wang, Xinbing Wang, and Arne Nilsson, “Energy-Efficient Bandwidth Allocation in Wireless Networks: Algorithms, Analysis, and Simulation,” in IEEE Transactions on Wireless Communications, Vol 5, no. 4, pp 1-12, April 2006.
- Wenye Wang and Ian F. Akyildiz, “A New Signaling Protocol for Intersystem Roaming in Next-Generation Wireless Systems,” in IEEE Journals on Selected Areas in Communications (JSAC), Vol. 19, No. 10, pp. 2040-2052, October 2001.
- Wenye Wang and Ian F. Akyildiz, “Intersystem Location Update and Paging Schemes for Multitier Wireless Networks,” in Proc. of ACM/IEEE MobiCom’2000, pp. 99-109, August 2000.
System and Applications
Advances in wireless networking technology as well as the development in lower-power devices and ubiquitous Internet have brought wireless techniques beyond conventional data communication and information technology. Driven by real-world demands, such as manufacturing, health care, and robotics, power surveillance systems, and many emerging applications are characterized by time- and data-sensitive applications. We are currently investigating several aspects toward system design and applications, which not only provides an opportunity to practice our study and to collaborate with other groups, but also offers a platform to have undergraduate students participated in research activities. The emphasis on this research is on developing a personal indoor wireless sensor network and applying to wireless network controlled systems.
An interesting and potential application of wireless sensor networks (WSNs) is visually (or virtually) tracking the person’s daily interaction with his/her habitat and monitoring the indoor conditions by the help of the sensors embedded throughout the home, building, etc. One interesting example of such applications is on Aging Services Technologies with a specific focus on In-Home Health Care Solutions for people of ages 65 and older. These applications naturally brings in the need for deployment of an “in-home” wireless sensor network. However, indoor environment is not a benign networking environment where several obstacles may render wireless communication impossible between node pairs. In addition, due to limited and irregular sensing ranges, placement of sensors becomes an important and challenging problem which may impact the accuracy of the collected data.
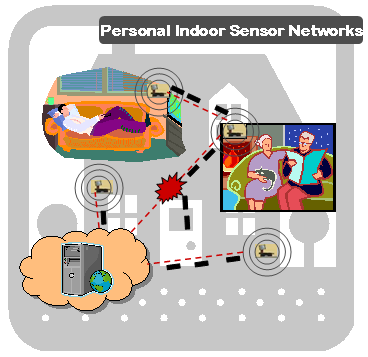
In the general case, basic parameters for an indoor sensor network can be impacts of node placement (position, orientation), transmission range / sensing range ratio, distance of reachability and degree of connectivity. Another interesting topic would be investigating how to preserve reliability within an in-home wireless sensor network with updated decisions on parameter settings (radio, llc/mac, routing, application etc). This would be very useful since home itself is like a living organism. Furniture might move, neighbor might start to emit noise at certain hours, heat can change etc. Or, increased reliability might be needed when an abnormal state is detected. To investigate and characterize the properties of Personal INdoor Sensor networks (PINS), we establish an indoor sensor testbed.
iSpace is a network based integrated navigation system for unmanned ground vehicles (UGV) developed at the Advanced Diagnosis, Automation, and Control (ADAC) Laboratory. It has different modules combined together to guide a UGV from one point to another in the space of interest, where the navigation intelligence lies on a controller away from the UGV. There are some rules to decide the motion. The UGV has to reach the destination as quickly as possible and avoiding the obstacles in the space. The destination point is chosen by the user via any remote computing interface in the world using the iSpace GUI on the Internet. The figure below explains iSpace structure.
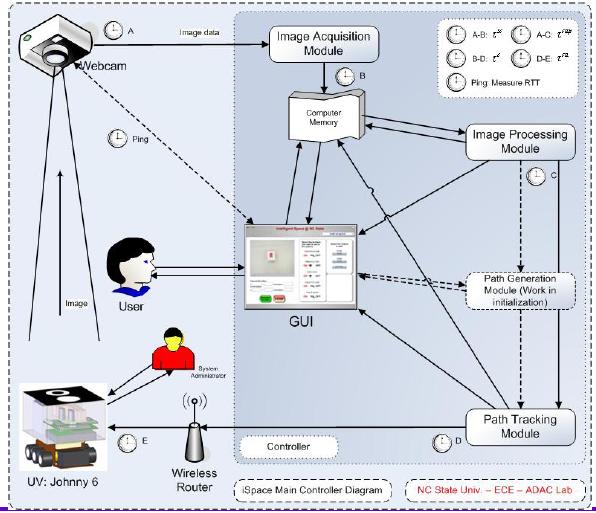
STEP2 is integrated with iSpace to provide dynamic and adaptive protection over the wireless part between the controller and robots. The whole iSpace flow diagram with the STEP2 is as follows. Presently, iSpace supports only confidentiality feature by using Data encryption standard (DES) and 3DES encryption/decryption algorithms.
Publications
- Rachana Gupta, Avesh K. Agarwal, Wenye Wang, Mo-Yuen Chow, “Characterization of data-sensitive wireless distributed networked-control-systems,” to appear in the Proc. of the 2007 IEEE/ASME International Conference on Advanced Intelligent Mechatronics.
- Avesh K. Agarwal and Wenye Wang, “DSPM: Dynamic Security Policy Management for Optimizing Performance in Wireless Networks,” in the Proc. of IEEE Milcom’06, Washington, D.C. October 2006.