Research
This section shows the active research projects in our lab.
Post-Quantum Cryptography
Quantum computers will make all existing public-key schemes obsolete and generate a critical need to develop quantum-secure alternatives.
The primary purpose of this research is to design efficient post-quantum cryptosystems and to optimize them for low-cost, embedded, and real-time applications. Since Shor’s quantum cryptanalysis of factorization and discrete logarithm problems, it is known that the widely-adopted public-key encryptions like RSA and ECC fails to provide security under quantum computer attacks. Post-quantum cryptography seeks alternative constructions that can secure the cyberspace against the attacks of such powerful quantum computers. In our research, we focus on the two most promising post-quantum proposals: lattice-based and hash-based cryptosystems. While hash-based cryptosystems are regarded to be the most secure, lattice-based cryptosystems has a potential to be very efficient for hardware and software realizations. We provide optimized designs for the implementation of these two schemes. Our work proposes optimizations that can drastically improve the efficiency of hardware and software realizations of post-quantum systems and enables them for low-cost and energy-constrained embedded applications.
Our contribution is threefold, which are documented with three subsequent publications. We first analyzed the building block of lattice-based cryptosystems: polynomial multiplication with the number theoretic transform (NTT). We designed a novel hardware architecture for NTT multiplication and implement it on Field Programmable Gate Arrays (FPGAs). The design applies on-the-fly operand computation, improved memory organization, and simplified address generation techniques to reduce the number of slices, memory blocks, and memory accesses. We demonstrate that, compared to previous work, the proposed design can save up to 80% of these resources while still achieving a similar performance. Second, we implement a full lattice-based post-quantum digital signature scheme on FPGAs. This design is targeted for real-time systems like avionics and automotive, and it thus minimizes the latency of a digital signature generation. We propose a hardware/software co-designed system that is partitioned in such a way to maximize the efficiency of a given area for signature generation. The system applies an optimization using precomputation by mapping all input-independent operations to software running on a softcore microprocessor and by accelerating the latency-critical operations with a customized hardware. This approach drastically reduces the latency of signature generation up to 105. Third, we extend precomputation methodology on extremely constrained and energy-harvested embedded microcontrollers that run entirely of solar energy. This system computes post-quantum digital signatures using hash-based cryptography. We identify energy-friendly intervals in the energy profile that favors precomputation, which improve the energy footprint of the hash-based signature generation up to 11.9.
Lightweight Cryptography for IoT
As small things connect to internet, their security mechanisms should be tailored to match stringent area and power constraints.
The primary objective of this project is to design low-cost hardware architectures for security solutions on the Internet-of-Things (IoT). Constrained platforms like Radio Frequency Identifiers (RFID), Near Field Communication (NFC) tags, and Wireless Sensor Nodes (WSN) forms the IoT that enable a myriad of brand new applications. These platforms require a simple yet effective security solution thus public-key infrastructures are typically infeasible for them. Unfortunately, even the traditional symmetric-key systems based on AES and 3-DES are too complex to be used in such low-cost architectures. Lightweight cryptography addresses these constraints by proposing alternative cryptographic building blocks that are suitable for the constrained IoT nodes. Our research sought ultra-low-cost hardware designs for FPGA based nodes that will activate lightweight security solutions.
At its core, our work uses a block cipher called SIMON, which was recently developed by the National Security Agency (NSA). We proposed three contributions based on this design which are documented with three subsequent publications. We first demonstrate that the SIMON algorithm yields extremely small architectures on FPGAs. We apply bit-serialization, a design method to process one output bit in one clock cycle, on SIMON and quantify that the resulting architecture is indeed the smallest block cipher ever published at 128-bit security level. Second, we extend this design into a flexible yet still compact architecture that can implement all configurations of SIMON including all key sizes (from 64-bits to 256-bits) and all block sizes (from 32-bits to 128-bits). This design is still smaller than the majority of block ciphers and all hash functions at equivalent security levels. Third, we propose BitCryptor, a multi-purpose, bit-serialized, compact processor for symmetric-key cryptographic applications on reconfigurable hardware. The proposed crypto engine can perform pseudo-random number generation, strong collision-resistant hashing and variable-key block cipher encryption. The entire crypto engine is 95 slices (187 LUTs, 102 registers), which is 10× smaller than the nearest comparable multi-purpose design.
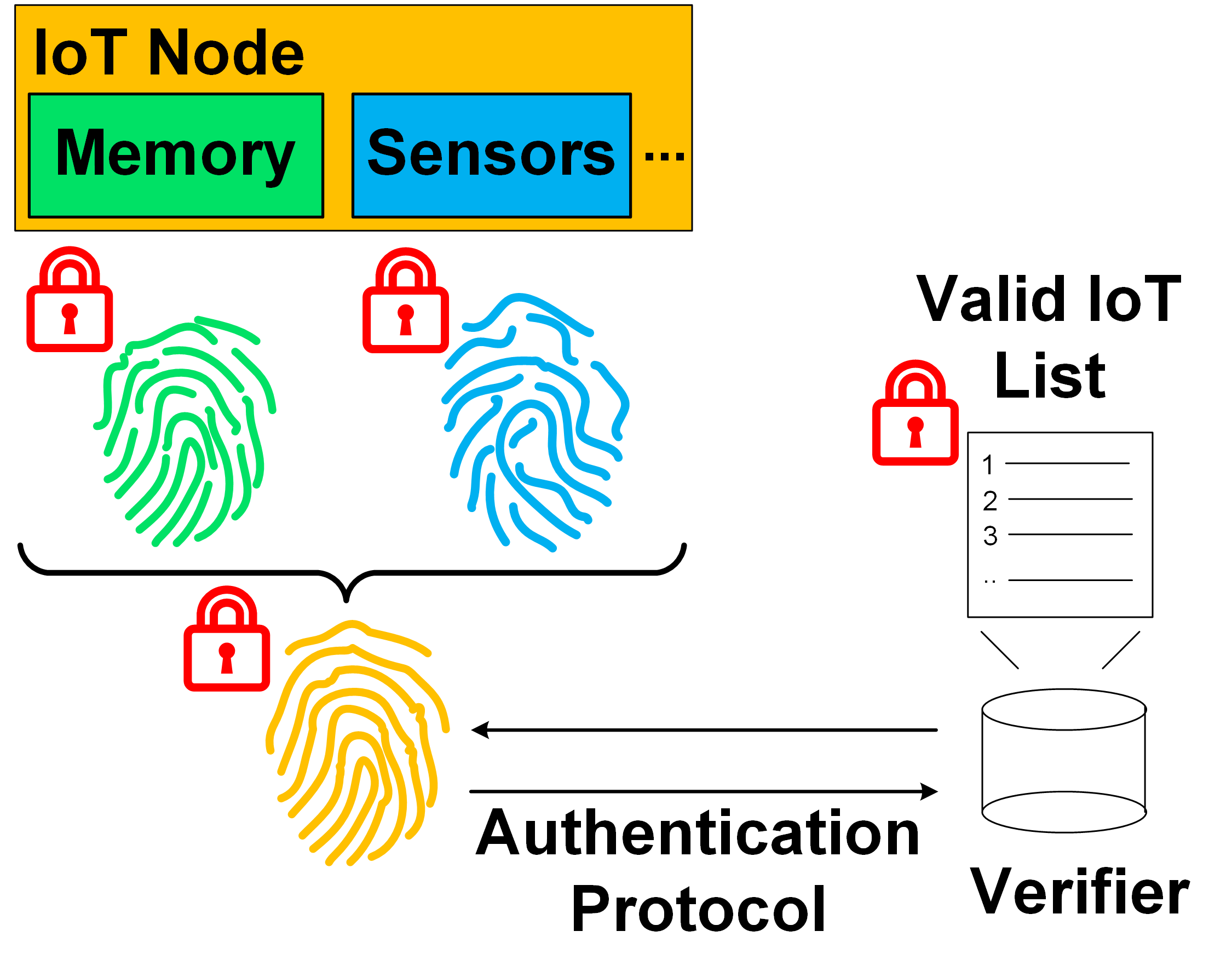
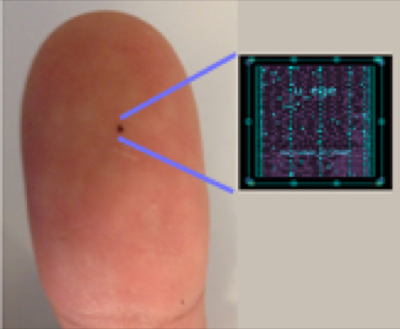
Physical Unclonable Functions (PUFs)
PUF is a new technology to combat counterfeit electronic devices by building on-chip digital fingerprints from inherent manufacturing variations.
The process variations during the manufacturing of a digital device causes deviations from its intended electrical characteristics. These variations are due to random events like micro-vibrations and lithographic errors which are unavoidable and hard to precisely model. Therefore, it is infeasible to clone an exact replica of a digital device by intentionally replicating its specific process variations. Physical Unclonable Function (PUF) technology exploits these variations to generate a unique and hardware-intrinsic identifier from a physical platform. The generated identifier is a silicon fingerprint of the device and can form its root-of-trust. Thus, PUFs provide a new method to generate secret values inside hardware. Although it is a very promising concept, the suitability of these methods are unclear on a wide range of electronic devices.
PUF HARDWARE
The primary objective of this project is to design novel PUF constructions on new hardware platforms. Our contribution is threefold, which are documented with three subsequent publications. First, we propose a o novel PUF construction on a microelectromechanical system (MEMS) sensor, an accelerometer, and utilize its process variations to generate digital fingerprints. This is achieved by measuring the accelerometer’s unique response to an applied electrostatic impulse and by measuring its inherent offset values. We then proposed PASC, a novel PUF construction on FPGAs by using the critical timing path violations of a custom instruction execution. This PUF is tightly integrated into the System-on-Chip (SoC) design and can be issued by instructions of a soft-core processor. Third, we propose a synchronous variant of the FPGA PUF that uses the principles of time-to-digital converters. Our solutions enable practical, run-time physical evaluation of the hardware via PUFs and it allows flexible post-processing mechanisms using software. We used advanced statistical methods to quantify the quality of our PUF designs and revealed that the digital responses of PUFs have the potential to fingerprint trillions of electronic devices.
PUF PROTOCOLS
The primary purpose of this project is to devise novel protocols and complete systems with new cryptographic primitives for next-generation applications. Our contribution is fourfold, which are document with three subsequent publications and one granted patent. First, we demonstrate the end-to-end design of a cryptographic protocol from theory to its practical application: reported results include a full protocol analysis, the design of its building blocks, their integration into a constrained device, and finally its performance evaluation. The protocol is provably (information-theoretically) secure and we verify that it does not leak any privacy information during the authentication test. The proposed system also describes a novel error correction mechanism for key generation which has an improved error coding efficiency. Second, we extend this protocol with a channel-based key-agreement (CBKA) scheme that allows to generate session keys to provide outsider chosen perturbation security. Third, we propose a method for remotely checking the integrity of components within a complex system that is deployed in the field. The proposed solution fuses the information of key components into a combined board identifier and performs a lightweight cryptographic protocol for its validation. Fourth, we propose a framework of cryptographic protocols for unified near field communication (NFC) tags. This framework addresses the challenges of current systems: a unified tag serves multiple applications from multiple vendors thus it should ensure that no sensitive information is leaked between those entities.
Side-channel Attacks
Side-channel attacks use implementation vulnerabilities to break cryptographically secure algorithms.
Although cryptograpic algorithms can provide theoretical guarentees, their practical implementations can leak secrets through side-channel information. Physical side-channels are especially important for IoT and CPS applications where the correlation of secrets to execution time of the algorithm, power consumption of the device, and electromagnetic radiation of the hardware can be exploited to implement side-channel attacks. We are using advanced side-channel attacks to break cryptographic and other state-of-the-art systems. Our most recent research showed that a promising lattice-based Post-Quantum encryption proposal, which provide theoretical security against quantum computers, can be broken with a side-channel attack that costs less than 100$ worth of equipment. We furthermore showed that this attack can be mitigated by a low-cost hardware countermeasure that uses an algorithmic specific opportunity to randomize internal secrets of the encryption. More information will be added to this project following the publication of the related work.
Secure Computer Architectures and Malware Detection with Machine Learning
New micro-architectural attacks encourage designers to detect zero-day malware through machine learning.
For the last four decades, computer architectures have been optimized for performance and cost with a rule of thumb that says “make common case fast”. As we use computers in everyday applications, a third dimension, security, have appeared, and adversaries started to exploit the variation introduced by performance/cost optimizations. New micro-architectural attacks such as covert-channel and rowhammer malware are such examples that are hard to detect using conventional malware analysis techniques. On the other hand, these attacks have to manifest themselves in someway (eg. deviations in power consumption) as they introduce anomaly to system’s activity. Machine learning methods can analyze the behavior of trusted states and identify if/when it alters from expected conditions, enabling the discovery of zero-day malware. More information will be added to this project following the publication of the related work.